Bypasses
Some content on this page is taken from --> https://medium.com/@meshal_/pentesting-non-proxy-aware-mobile-applications-65161f62a965
How to verify if the application is non-proxy aware?
When running the application, you should either see your HTTPS data in Burp’s Proxy tab, or you should see HTTPS connection errors in Burp’s Event log on the Dashboard panel. Since the entire device is proxied, you will see many blocked requests from applications that use SSL Pinning (e.g. Google Play), so see if you can find a domain that is related to the application. If you don’t see any relevant failed connections, your application is most likely proxy unaware.
As an additional sanity check, you can see if the application uses a third party framework. If the app is written in Flutter it will definitely be proxy unaware, while if it’s written in Xamarin or Unity, there’s a good chance it will ignore the system’s proxy settings.
Decompile with apktool
apktool d myapp.apk
Go through known locations
Flutter:
myapp/lib/arm64-v8a/libflutter.soXamarin:
myapp/unknown/assemblies/Mono.Android.dllUnity:
myapp/lib/arm64-v8a/libunity.so
Solution
Using ProxyDroid or similar tool on Rooted Device:
Use ProxyDroid (root only). Although it’s an old app, it still works really well. ProxyDroid uses iptables in order to forcefully redirect traffic to your proxy.
Setting up VPN Server and diverting traffic that way
Set up a VPN on your VM or Host wherever you are testing from, following this guide:
After setting up the virtual machine and VPN server, now we need to force all the traffic that goes through our VPN to be directed to port 8085 which is what our Burp Suite proxy is listening on:
Iptables
Flush all previous rules to start fresh:
Set accept all policy to all connections:
Forward all HTTP and HTTPS traffic from the VPN network interface tun0 to the listening port in Burp Suite 8085:
Re-applying iptables rules was needed every time the virtual machine was rebooted.
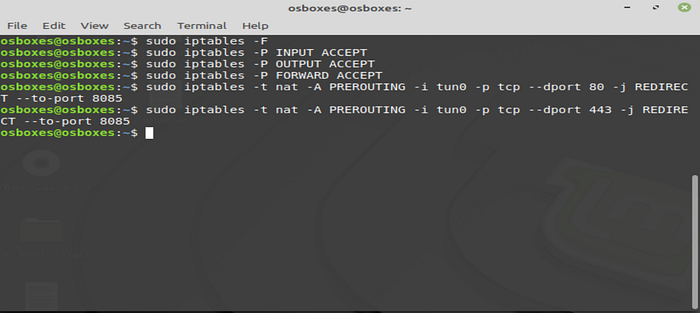
In this way, we are forcing all traffic from the mobile phone to go through Burp Suite proxy.
Configuring Burp Suite Listener:
Set Burp Suite to listen on port 8085 on all interfaces, but we still have an issue to deal with which Burp Suite can’t resolve the requests to a specific IP.
Configuring Burp Suite to resolve the domain/IP :
In Proxy tab go to Edit then click Request handling. After that, provide the destination IP (The IP which the mobile application sending its requests to).
Check “Support invisible proxying”.
Last updated