Decrypting iOS Apps
This Writeup belongs to: (its just pasted here for my quick reference, I dont own this writeup)
Scenario
jailbreak -> select tool -> dump
Instruments
You have 3 options:
frida-ios-decrypt (jump to How to Use "frida-ios-decrypt")
Clutch (jump to How to Use "Clutch")
Additionally, you need SSH (OpenSSH) installed on a jailbroken iPhone to be able to copy dumped files.
Overview
An application from Apple App Store is encrypted with a hardware-backed cryptographic scheme. More precisely, an executable section of the O-Mach binary inside the IPA package is encrypted, and the decryption key is accessible only on a particular device on the hardware level (Secure Enclave). But if you wonder whether it is possible to decipher an application downloaded from Apple App Store to carry out static analysis - yes, it is possible.
In the annex, you can find How To Jailbreak iPhone 12.x and How to Fix Entitlements.
How Tools Work
All tools leverage a simple principle: these tools dump a decrypted binary from the running context in the memory. It is possible because the binary MUST be decrypted before it could be even run, and the binary is dumped into a file.
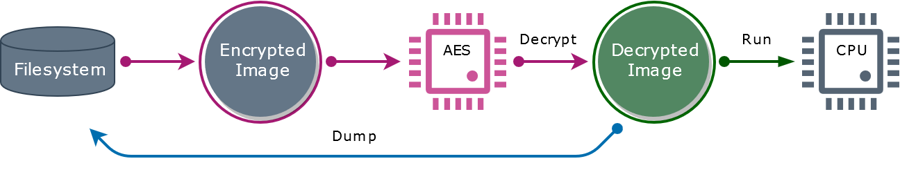
You MUST jailbreak iPhone to dump decrypted executable region to the filesystem. There is no way to easily decrypt an application by any kind of magic tool on a personal computer.
There are 2 approaches to dump deciphered executable region from memory to the filesystem. All of them require superuser privileges either to trace a process, or to inject a dynamic library.
Approach #1: attach to a process
Clutch and frida-ios-decrypt work this way.
The tool (tracer) attaches to a running process (tracee).
The deciphered executable is dumped from the memory into a file.
Step 1 (tracing the process) needs superuser privileges, that's why iPhone must be jailbroken.
Approach #2: library injection
dumpdecrypted.dylib works this way (through DYLD_INSERT_LIBRARIES).
An application starts with a dynamic library linked into it.
The dynamic library dumps decrypted executable right from the application user space memory.
Superuser privilege is needed to inject a custom dynamic library into the process memory.
How to Use "frida-ios-decrypt"
Prepare USB and SSH
The main script of "frida-ios-decrypt" dump.py uses the frida package which communicates with the device via USB. When the application is successfully dumped, files will have been copied from the device via SSH (scp) to the temporary folder. To summarize, your iPhone must be accessible via both USB and SSH.
An official guide suggests to set up SSH over USB, but that way seems to be a bit complicated. I found the easier way which is to connect an iPhone to your local network (connect to the same WiFi network) and modify dump.py as the following to allow the script to connect to the phone directly over your local network:
Steps
Follow the frida-ios-dump installation guide.
frida-ios-dumplooks for a device using SSH. Use "SSH over USB" approach, or connect your device to a local network and fixdump.py(see Preparation above).List running processes:
Dump the target process:
or
Successful log
Troubleshooting
Device is not found via USB
Ensure that you installed USB drivers for iPhone.
Also, if you're on Windows Subsystem for Linux (WSL), you would be unable to run "frida-ios-dump", because there is no USB drivers for iPhone under WSL, therefore iPhone cannot be enumerated. (Not sure about WSL 2 though).
Device is not found via SSH
Either way, if dump.py cannot connect to a device, you will see the following error:
or
Check whether you use a correct IP address in dump.py for your iPhone.
On iPhone: go to Settings -> WiFi -> (i) -> get the IP.
Verify the connection:
ssh [email protected]Password: alpine
How to Use "Clutch"
IMPORTANT: On iPhone 12.x you need to fix entitlements ⬇️.
Build and install the Clutch tool.
List the processes:
Dump the process obtaining decrypted binaries:
"3" is the number of the application from the
Clutch -ioutput.
How to Use "dumpdecrypted.dylib"
IMPORTANT: On iPhone 12.x you need to fix entitlements ➡️️.
Download dumpdecrypted.dylib to a computer.
Copy
dumpdecrypted.dylibto the system path on the phone via SSH usingscptool:Choose a path, kind of
/usr/lib, not$HOME, to evade problems with kernel sandboxing.Run the application with
dumpdecrypted.dylib:
How to Jailbreak iPhone 12.x
Download Chimera IPA package.
Download Cydia Impactor.
Deploy Chimera package to iPhone using the Cydia tool (it will ask your Apple ID, it can be ANY free Apple ID).
On the iPhone: go to the Chimera and press a button "Jailbreak".
Sileo marketplace app appears after the jailbreak is installed.
Go to the Sileo application.
Find and install Frida and OpenSSH (sshd).
Install OpenSSH in the Sileo application
How to Fix Entitlements
The big advantage of "frida-ios-dump" against the "Clutch" and "dumpdecrypt.dylib" is that it doesn't need to fix entitlements of the target app.
Entitlements are special properties assigned to each application in iOS. Entitlements are signed and basically, it's not possible to change them without a jailbreak.
In iOS 12.x default entitlements of application don't allow tracing. In the case of Clutch you are going to see the following error:
Steps to fix entitlements:
Dump the current entitlements of the target application:
Fix entitlements adding the following line to
targetapp-ent.xml:Assign new entitlements:
Last updated
